PAM - why NOT to save passwords in Excel
PAM or Privileged Account Management is a tool that helps to secure and manage administrator passwords, access to sensitive corporate data and accesses for service and application accounts from a single console, with clear division of authority and detailed audit.
Most common practice for storing account information is by keeping them in excel sheets or in applications such as KeePass or LastPass. This practise is not recommended, since those servers are primary goal and easy to be accessed by hackers. Passwords are also poorly managed, there is no automation of password changes, no audit records, and little to zero possibility for setting adequate permissions for data access.
This issues are addressed with Thycotic solution - Secret Server. Secret Server is an enterprise-class password Management Vault, for lock down sensitive account passwords on-premises and which integrates with Active Directory. Secret Server:
- sufficiently secures sensitive information,
- automate privileged account discovery and password changing
- provide full audit reports for compliance
- control what admins can do with privileged accounts.

Secret Server runs within Microsoft IIS server and secures your data in Microsoft SQL database. All sensitive data are encrypted using AES 256 and SSL encryption. Secret Server can be accessed via web browser and is supported by Internet Explorer, Google Chrome and Firefox. It is also enables mobile or desktop app.
With Secret Server it is possible, to use API for features integration, application access and scripts into Secret Server so they can be easily accessed via Secret Server app.
Secret Server users are able to authenticate with Microsoft Active Directory and with two-factor authentication (RADIUS, soft token). Philosophy behind privileges is based on the RBAC model and supplemented by individual approaches for each set of sensitive information which enables creation of role-based permissions for each user.
Sensitive information can be stored in folders in the tree structure and drive further permissions for each folder or sensitive information. Inherit permissions within the tree is then a matter of course. Secret Server enables identifications of user roles within individual application and it can identify sensitive information and proceed accordantly.
Secret Server Architecture
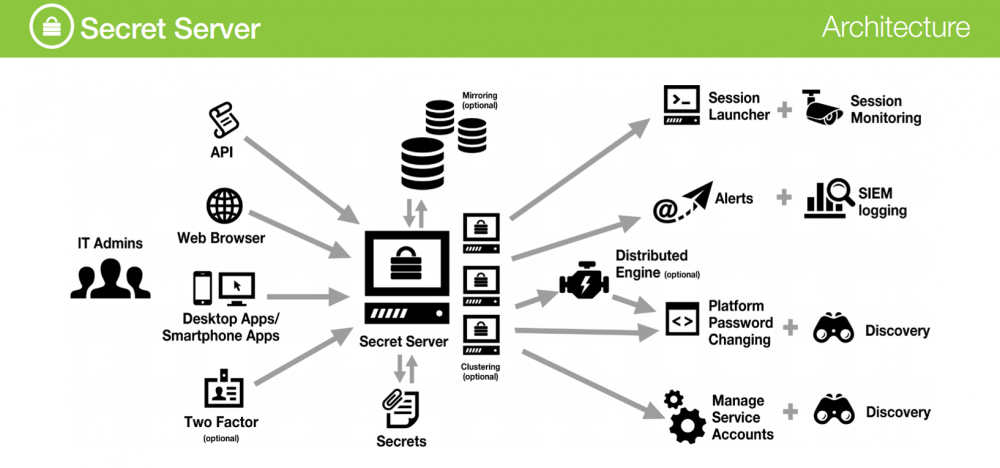
Secret Server is not only the Vault for securing sensitive data and database access information, its benefits includes:
- Advanced methods for securing access to the actual password, which enables password change after each use; custom approval workflows (Check Out, Request Access, Require Comment); option to force a comment for every time password is used.
- Option to automatically open the management console systems and applications. These consoles include Microsoft RDP, Microsoft SQL Server Management Studio, SSH console (Putty), Microsoft PowerShell. It is possible to use extensions to browsers that automatically fills in the login information into web forms. It is also possible to define custom console. With this feature, the administrator does not need to know the password itself, because the console automatically opens and the stored information.
- Option to use Secret Server as a proxy for the RDP and SSH connections. Which enables possibility to automatically terminate connections to systems which were initiated by itself.
- Session recording and monitoring for individual RDP or SSH connection. With this feature, you will keep records in the form of video. It is possible to watch these live console and in the case of undesirable activities to interrupt the connection and deny access. If SSH is possible to keep records of text input and output in the console.
- Automatic password changing and password validation enables advanced security policy for passwords change while maintaining a high complexity and sufficient password length. Regular password validation will prevent any unauthorized attempt for password change.
- Automatic discovery enables periodically check of stored data in Active Directory and defined network segment and monitoring the emergence of new privileged accounts.
- Accounts management. Secret Server enables automatic periodical password changes for AD and other applications, which is most beneficial for Windows Services, Scheduled Tasks or the IIS Application Pools, where regular password change is a challenge.
- Integrate with SIEM and vulnerability scanners for heightened security. Secret Server stores all audit information in the standard syslog and can be subsequently processed in SIEM systems.
- Seamless Disaster Recovery futures as are Database Mirroring, AlwaysOn, SQL clustering and Geo-replication, Front-end clustering for high availability, Automatic backups, Clear text export and Remote DR site support.
PAM should be standard in every IT department
Thycotic Secret Server enhances security for privileged accounts and automates common tasks with these approaches. A great benefit is the ability to selectively change passwords, cancel access to the administrator, who is leaving the company and protect your data against targeted attacks by former employees or former technology suppliers.
By using Secret Server it is possible to get rid of “sticky notes” with credentials on users screens, accounting department will no longer need to re-enter PIN codes to individual bank accounts, Shared accounts access to marketing team and passwords to social networks can be managed easily.
Secret Server applies basic layer of security for privileged accounts, which are main target for cyber-attacks.

Don't let your company be the next target! Contact us for detailed presentation and free trial: SI-info@alef.com