The main purpose of the ALEF OctoShield service is to provide a higher security standard for end devices connected to your network or connecting to the Internet from any location. Using our service, you will be protected from a vast majority of malicious software used by the attackers for engaging in cyber-attacks.
ALEF OctoShield

We use a combination of cloud products made by Cisco Systems – Advanced Malware Protection (AMP) and
Umbrella – offering features going beyond standard antivirus programs. Along with ALEF’s security monitoring, we provide customers with very strong and continuous protection from security incidents.
INCLUDED IN THE SERVICE
- Continuous protection of end user devices utilising modern cloud products made by Cisco Systems — Antimalware Protection for Endpoints (hereinafter AMP4E) and Umbrella.
- Quick and very effective blocking of any cyber attack on end devices, regardless of whether they are connected to the Internet via your network or outside it.
-
In-depth explanation of cyber attacks on endpoint devices and recommendations on how to prevent such attacks in the future.
- Cooperation provided by our experts in implementing preventive measures against further attacks.
WE OFFER SECURITY MONITORING IN TWO VARIANTS – BASIC AND PLUS
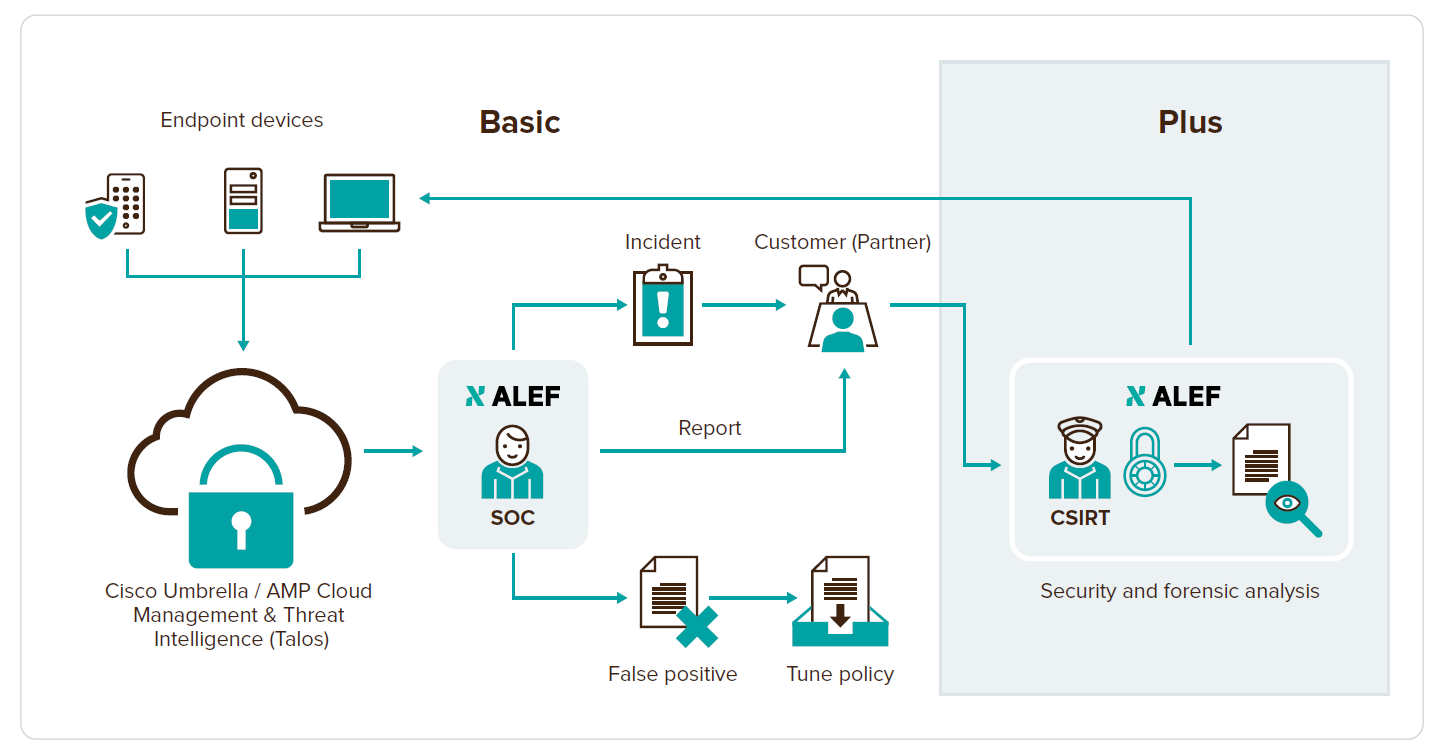
 ALEF OctoShield Basic | This variant includes:
ALEF OctoShield Basic | This variant includes:
-
Initial activation of AMP4E and Umbrella, where our professional team analyses the current protection status of your network and end devices, proposes the best possible scenario for implementing these two cloud products and fine tunes them to your needs.
- Continuous and automatic protection of end devices from security attacks. The protection works even where a user works outside the company, e.g. home office.
- Continuous monitoring and evaluation of security incidents detected by AMP4E and Umbrella on your end devices by the security team at ALEF Security Operations Center (SOC) in 8×5 mode.
-
Basic analysis of detected security incidents on end devices, particularly malware, command, and control callbacks, cryptomining.
- Distribution of regular weekly reports featuring an overview of security events detected on your end devices.
- Forwarding of information on the occurrence, impact, and security risk of a confirmed security incident, including proposals on how to proceed in a specific matter.
 ALEF OctoShield Plus | This variant includes the ALEF Incident Response service:
ALEF OctoShield Plus | This variant includes the ALEF Incident Response service:
- Resolution of security incidents, including implementation of corrective measures by the ALEF CSIRT security team, which is a registered member of the Trusted Introducer international organisation specialising in cyber security
- In-depth analysis of the malicious code identified in your network by the ALEF CSIRT team
- Security Scan, i.e. regular preventive daily or monthly security scanning of your communication and system infrastructure by a specialised tool; we will provide you with an overview of vulnerabilities of your network and an assessment of their criticality.