ALEF OctoShield
Continuous protection against various types of malware that attackers try to stealthily install on your computer.

OctoShield price for one device per month = price of a good cup of coffee
- Why is defending against cyber threats a critical area for any company, regardless of size?
- I have antivirus installed on my company computer, I use the security features built into the computer's operating system, and I use two-factor authentication when accessing company resources, isn't that enough?
- We have invested heavily in protecting our central IT from cyber attacks. Why isn't that enough and should we extend protection to personal computers?
- It all sounds complicated, where do I even begin to build cyber protection?
- How long does it take to get OctoShield up and running? And what about employees working in the home-office?
- What exactly do I get in OctoShield?
- What happens if I am attacked by a cyber attack?
Why is defending against cyber threats a critical area for any company, regardless of size?
Analytical reports from Gartner and Forbes suggest that 2021 was a record year for IT security breaches and cyberattacks. From everyday users to small businesses to large corporations, hospitals and government organizations, everyone is a target for cyber criminals.
I have antivirus installed on my company computer, I use the security features built into the computer's operating system, and I use two-factor authentication when accessing company resources, isn't that enough?
As cyber attacks become more sophisticated and easier for cybercriminals to launch, your current security measures may not be enough. Therefore, cybersecurity tools and practices need to be constantly monitored and updated to respond to new threats. It's hard for a company without highly specialized IT security experts to keep up.
It is important to remember that traditional antivirus solutions rely on virus detection based on so-called signatures, i.e. they look for specific characteristics of known threats in files. And while some antivirus solutions also offer so-called heuristic analysis, which tries to predict potential threats by analysing the behaviour of software on your computer in retrospect, this is still only a basic layer of protection that may not be sufficient at the moment given the rapid evolution of malware.
We have invested heavily in protecting our central IT from cyber-attacks. Why isn't that enough and should we extend protection to personal computers?
The prolonged COVID pandemic has forced many people to work from home over their internet connection, making their company computer an even more crucial part of the overall security of the business. This computer is not only used for business purposes, but also for personal use, with people accessing various content on the Internet through it, which can be very dangerous. It is therefore much more exposed to security risks than if it were only used in the company and connected to its internal IT network. It therefore deserves a greater level of protection from cyber-attacks than a conventional antivirus system can provide.
 It all sounds complicated, where do I even begin with building cyber protection?
It all sounds complicated, where do I even begin with building cyber protection?
 While building a cybersecurity team and implementing the necessary security solutions may take several months and involve a significant investment, your cybersecurity can be provided as a service. Just like you subscribe to software like Office 365 or services like Netflix, you can get cybersecurity for your computers, a service called OctoShield, from us for a monthly fee.
While building a cybersecurity team and implementing the necessary security solutions may take several months and involve a significant investment, your cybersecurity can be provided as a service. Just like you subscribe to software like Office 365 or services like Netflix, you can get cybersecurity for your computers, a service called OctoShield, from us for a monthly fee.
How long does it take to get OctoShield up and running? What about home-office employees?
We deploy OctoShield cybersecurity service in 1 to 5 days depending on the size of your organization. The service covers employees working in your office or at home using laptops or smartphones. We've got you covered.
What exactly do I get with OctoShield?

For a monthly fee per protected device, roughly equivalent to the cost of a cup of good coffee, you'll get a range of the following cybersecurity features:
Continuous protection from the various types of malware that attackers try to stealthily install on your computer
Continuous monitoring and blocking of communication from your computer to malicious Internet domains and websites, before your computer is infected with malware from them
send you a notification that a suspicious event or security attack has occurred on your computer and help you remove it if necessary
Our solution is based on products from Cisco Systems, a leading cybersecurity company that works with the most reputable companies and organizations around the world. Cisco Systems collects online information about security threats and attacks from millions of its devices worldwide in its database.

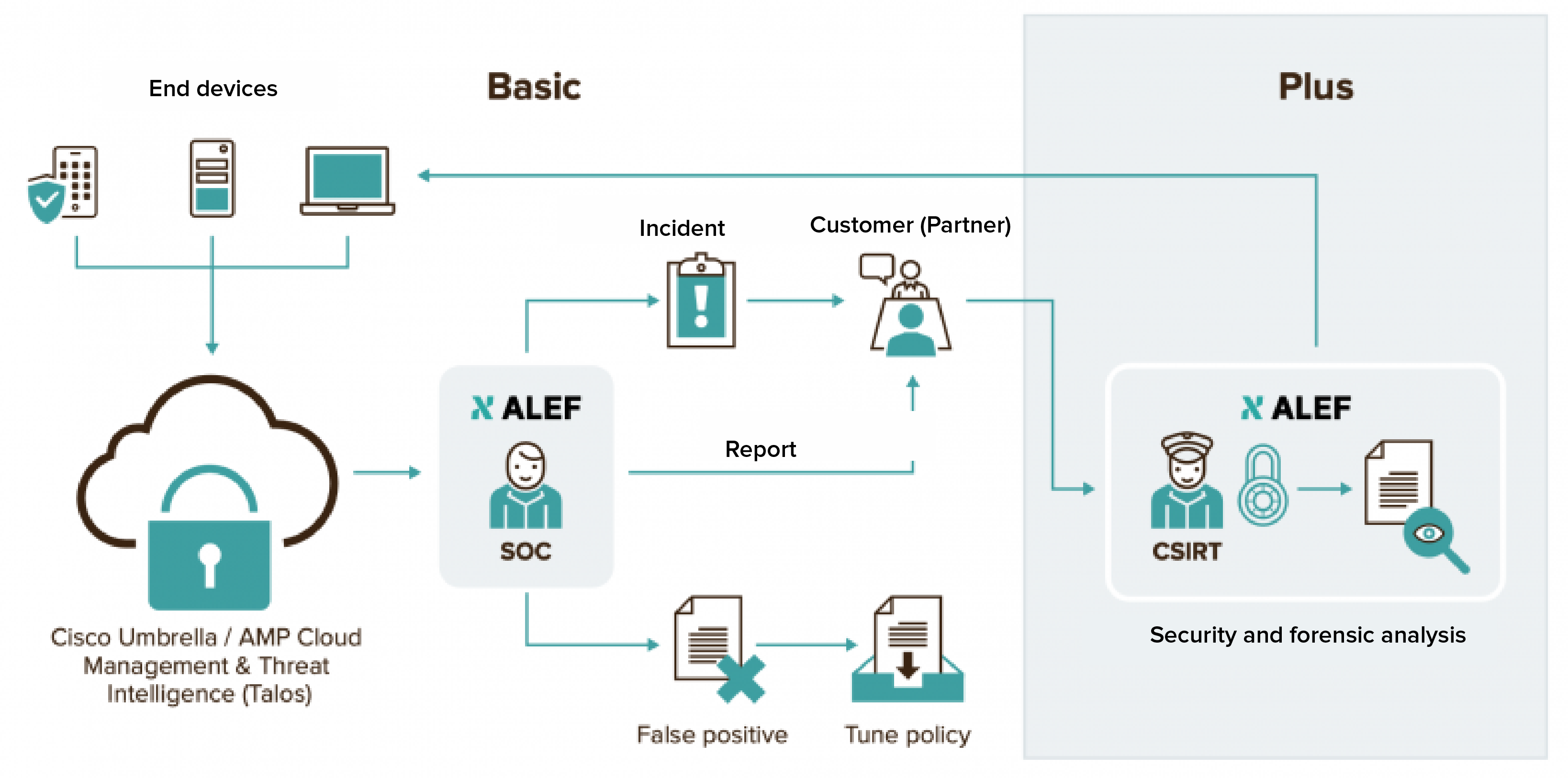
The Basic variant includes:
- Initial activation of Secure Endpoint and Umbrella, where our professional team will analyze the current state of your network and endpoint security, design the best possible scenario for implementing these two cloud-based products and customize them.
- Continuous and automatic protection of endpoint devices from security attacks. The protection works even if the user is working outside the company, e.g. in a home-office.
- Continuous monitoring and evaluation of security events recorded by Secure Endpoint and Umbrella on your endpoint devices by the ALEF Security Operations Center (SOC) security team in 8×5 mode.
- Basic analysis of recorded security events on endpoint devices, especially malware, command and control callbacks, cryptomining.
- Sending regular weekly reports with a summary of security events detected on your endpoint devices.
- Transmitting information about the occurrence, impact and security risk of a confirmed security incident with suggestions on how to further address the specific situation.
This option includes the ALEF Incident Response service:
- Security Incident Response, including implementation of corrective measures by the ALEF CSIRT security team, a registered member of the Trusted Introducer, an international organisation focused on cyber security.
- In-depth analysis of malicious code detected on your network by the ALEF CSIRT team.
- Security Scan i.e. a regular preventive daily or monthly security scan of your communication and system infrastructure with a specialized tool, where we will provide you with an overview of your network vulnerabilities and their criticality rating.
Law Firm
The customer was looking to increase the security of their IT environment. Discussions with him revealed that he needed to upgrade his firewalls and also focus on strengthening protection directly on his endpoint devices. The customer was attracted to OctoShield because of its advanced EDR (Endpoint Detection & Response) technologies, reputational protection over Domain Name System (DNS) and the added value of professional ongoing monitoring of security events by our specialists.
Bank
A customer experienced a security incident on their network caused by malware for which their existing IT resources were not prepared. Therefore, he needed a quick analysis within hours whether the malware still persisted in the network, tracing where the infection got into the network from and permanently protecting servers and end devices from further similar attacks. In addition to the advanced Cisco Systems security technologies included in OctoShield, the customer required continuous monitoring and reporting on the health of their IT.
Retail chain
The customer operates dozens of stores across the country and many of its employees work from home or on the road. They realise that strong security of the central IT infrastructure is not sufficient in this situation and that more security is needed for the end stations of the employees. What the customer appreciates about OctoShield is that it is a managed service, where the necessary know-how, software and capacity of the security staff is provided by an external service provider.
What happens if I am attacked by a cyber attack?
OctoShield protects your computer at all times with Cisco Systems technologies. These will automatically stop a cyber attack or significantly reduce its impact on your device. Our specialists will then send you information about what happened to explain the causes and consequences of the attack. If you choose to use OctoShield PLUS, they will then perform a forensic analysis for you and help you remediate the security vulnerabilities that led to the attack.
If you have any questions, do not hesitate to contact us!
Contact us:
Trust the Strong
ALEF Distribution CZ, s.r.o. | Pernerova 691/42, 186 00 Prague 8, Czech Republic