Identity Bridge

In the past few years, we have often heard about the use of user identity (not only) in firewalls. And yes, we can say from experience that the interest in integrating newly and previously implemented security technologies into enterprise identity databases is high. Why is this so? Because in the case of identity firewalls, you get greater visibility into the security policies you set up and the management of the entire ecosystem is significantly simplified. You can also eliminate some of the challenges of user segmentation.
Are you running ASA software on your firewalls but don't want to move to Next-Generation Firewall software FTD because you don't need it in your environment? And do you still want to:
- work with user identity
- increase security and visibility
- use user identity in security policies
- Replace the no longer supported Cisco Directory Agent (CDA) component that collects user identities for you
Alef Identity Bridge directly replaces Cisco Directory Agent.
Practical example:
Imagine the following practical scenario. A typical user today works on at least one endpoint device, which is most often a laptop, with which the organization's security policies are associated. In the case of a normal user, 802.1X can be used to assign that user to one of the networks with which a particular security policy will be associated. But how do we deal with situations where this user needs a specific security policy because he is different from his colleagues in the manner of accessing the datacenter?
In the case of a traditional firewall, the whole process of managing the security of access to company assets even from a single device is very complicated. The administrator must set up DHCP reservations for that user and their device separately in Wired, WiFi and VPN environments. With good network segmentation, in our example, there may be 3 static reservations on the DHCP server side for one device, one employee, in one L3 location. And these reserved IP addresses are further used in the firewall to create throughputs between user segments, to the datacenter or to the Internet.

Facilitating the process of managing the security of access to company assets.
I'm sure you are thinking of the following questions:
- But what if we have thousands of users and units or dozens of branches?
- What if a user has not one device, but two, and a different security policy must necessarily be applied to each?
- What does the IT process associated with the offboarding of an employee looks like from a HR/IT point of view?
- What if an employee is "sitting on two chairs" and needs to access different resources?
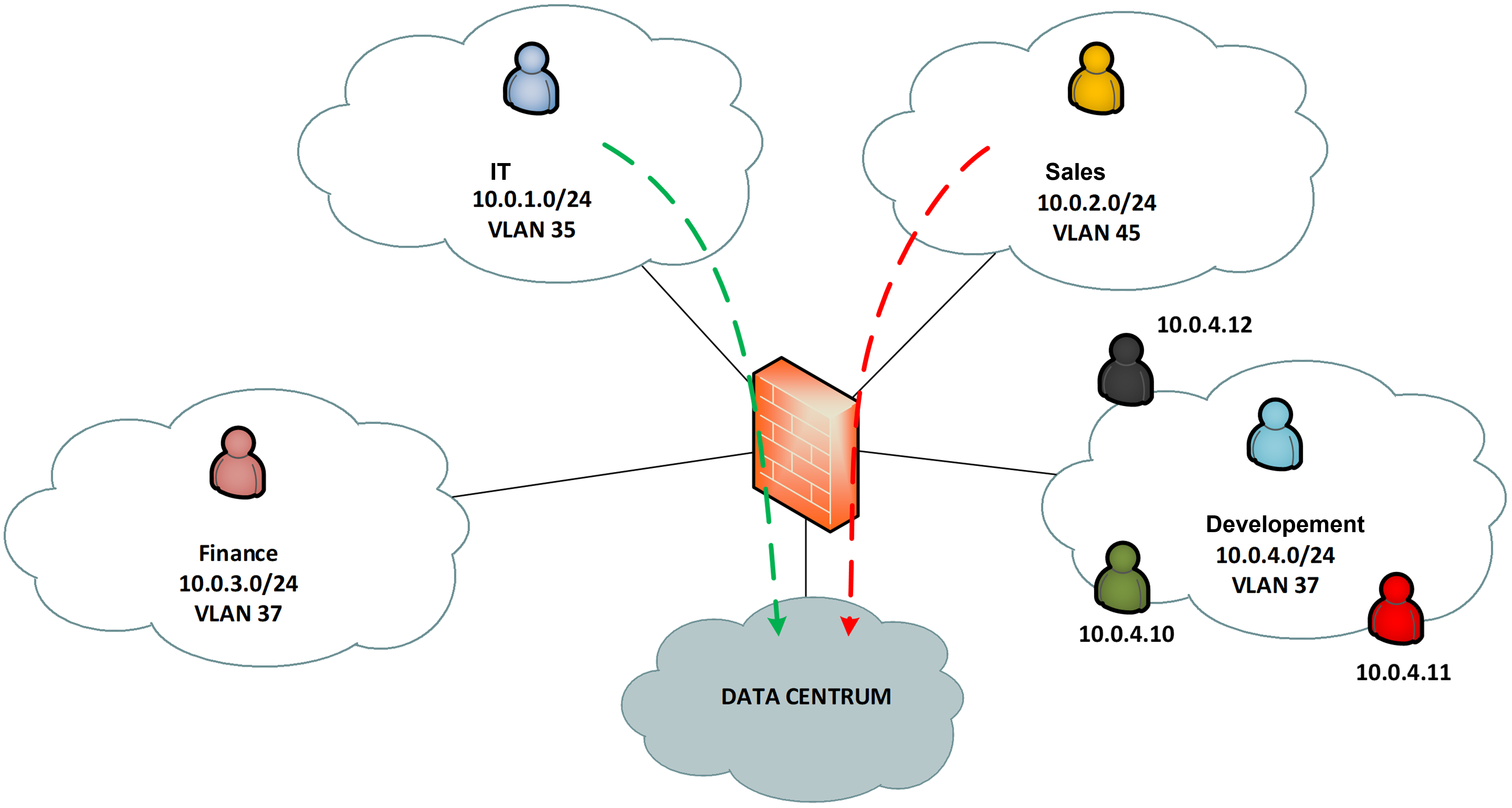
Will this "traditional" model still be sustainable? And is this even sustainable in terms of security, scalability and the burden it places on your IT staff?
Our Customers have been dealing with these issues and the end of life of the CDA component extensively, so with the support of Cisco, we came up with our own solution. This solution is a new software component that we have developed here at Alef Nula, called Identity Bridge. This component directly replaces the Cisco Directory Agent and allows customers to continue to work with user identity on Cisco Secure Firewalls with ASA software.