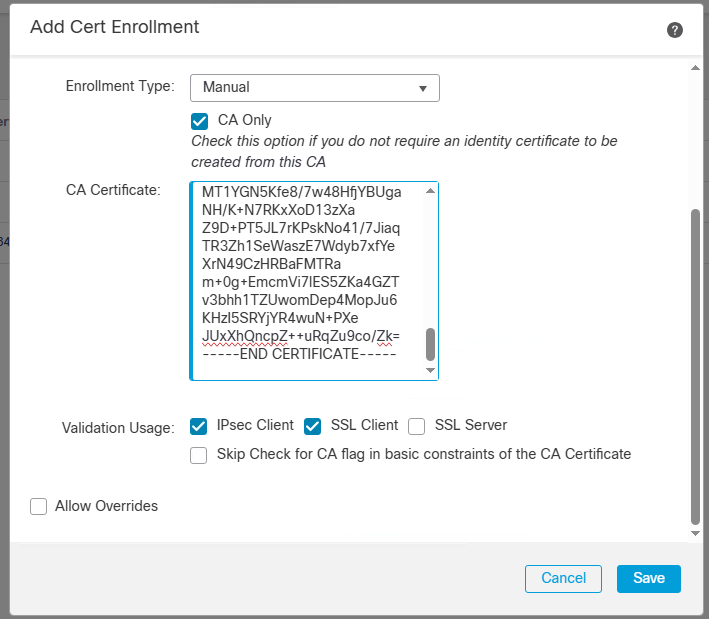
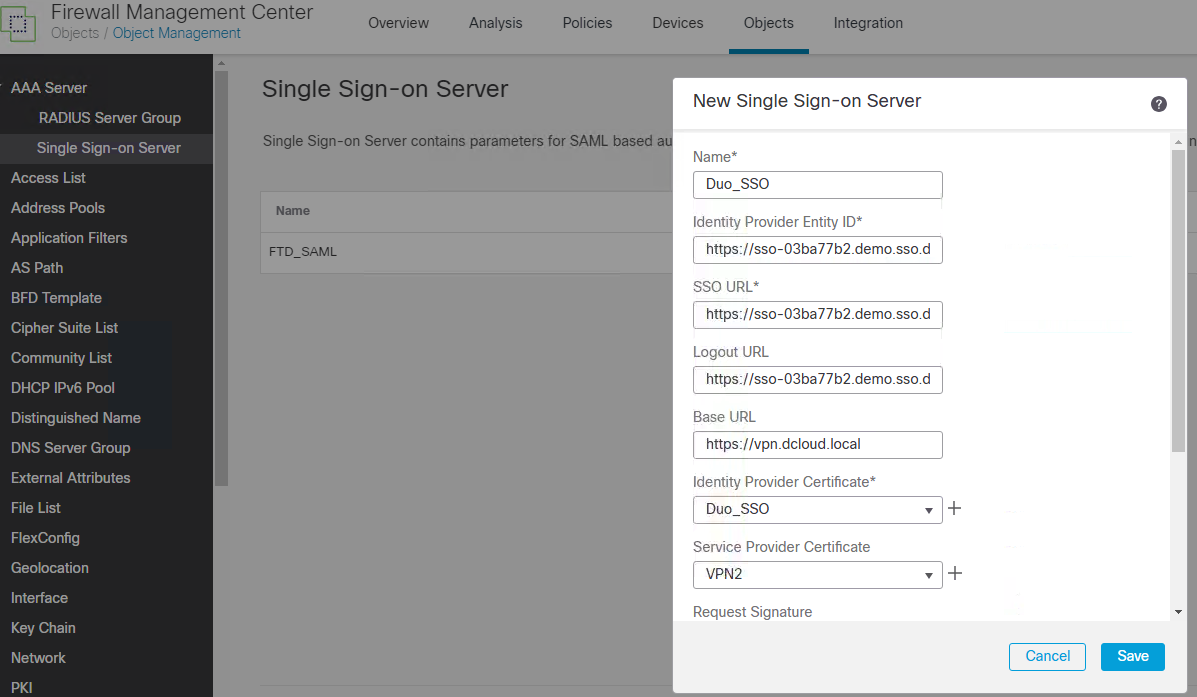
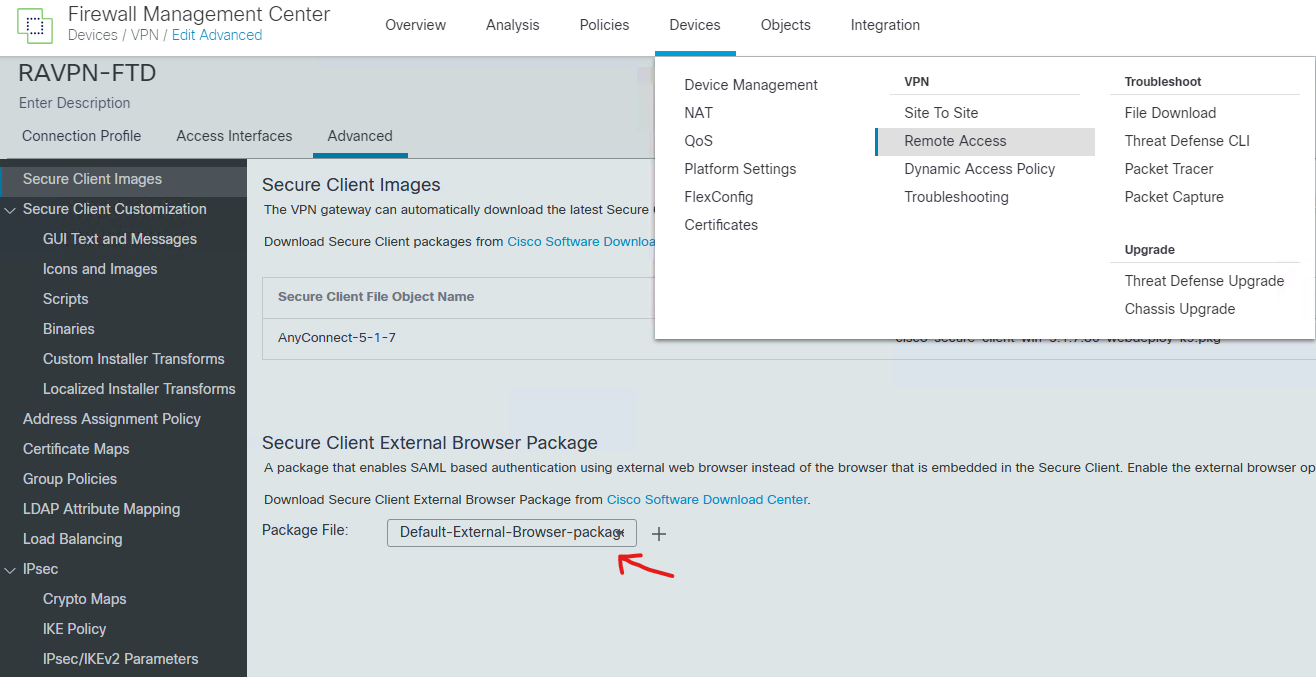
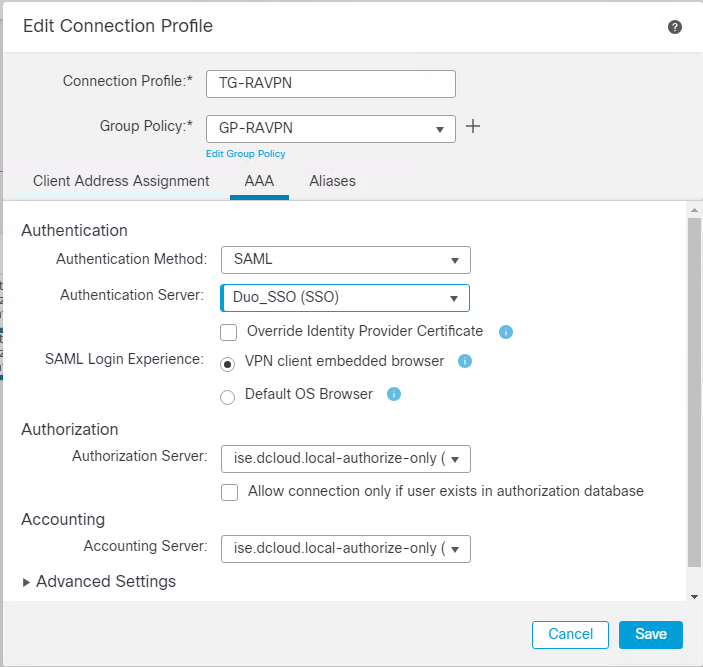
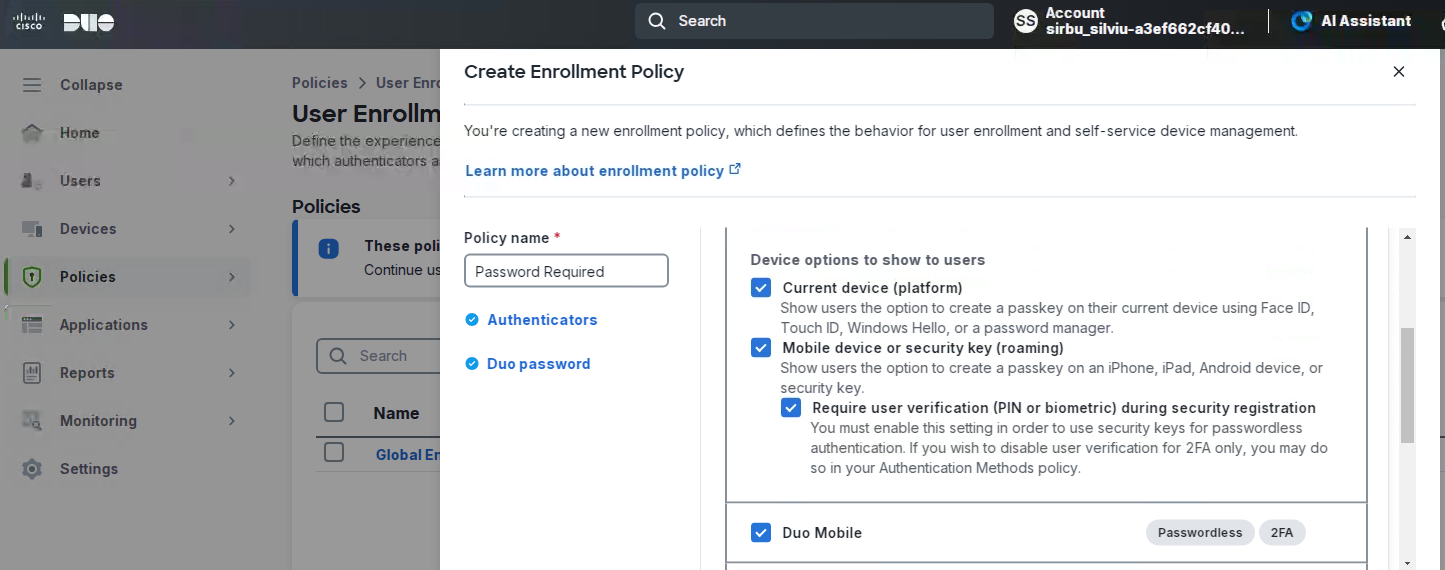
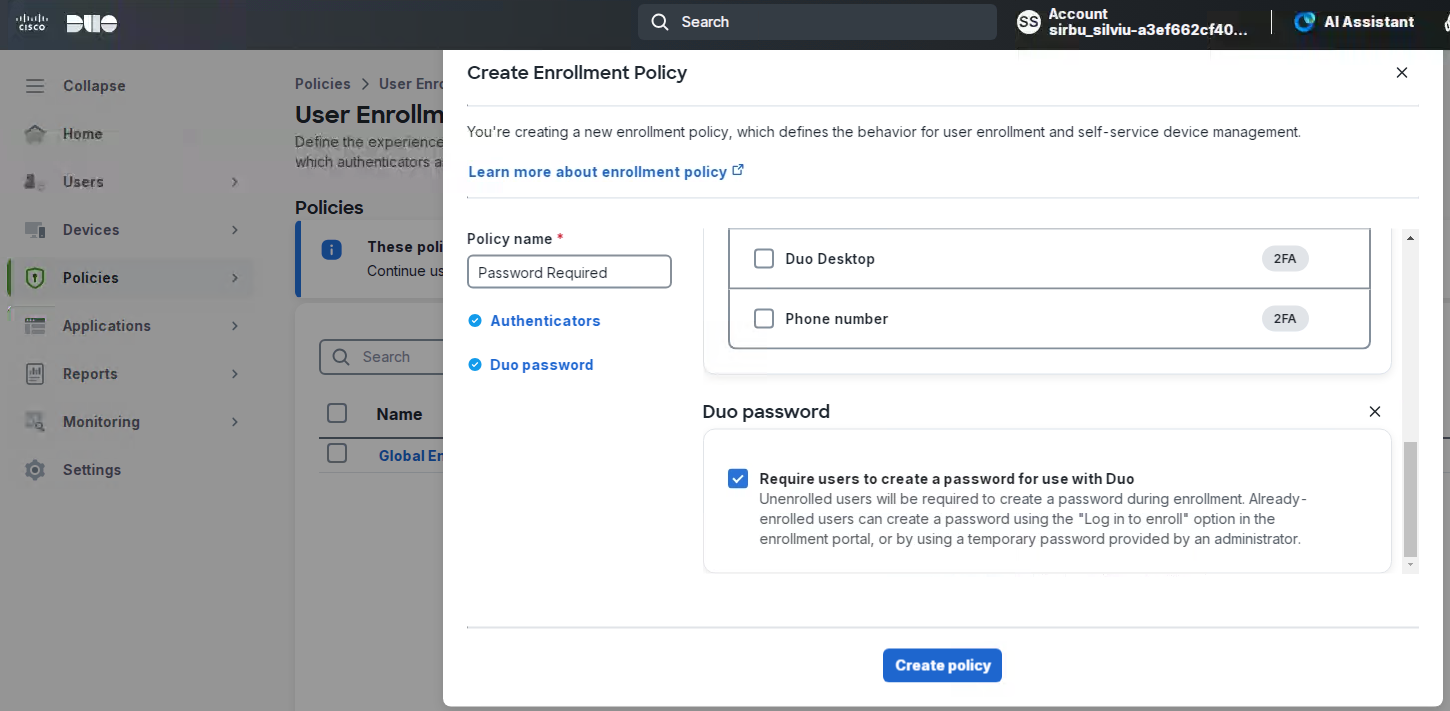
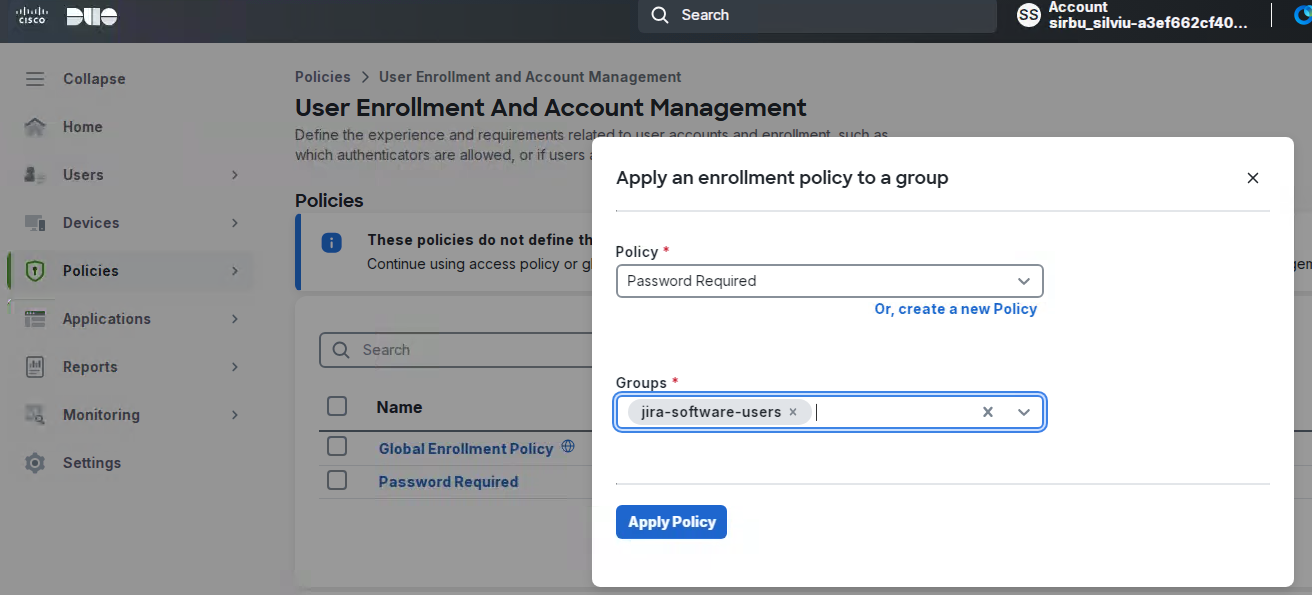
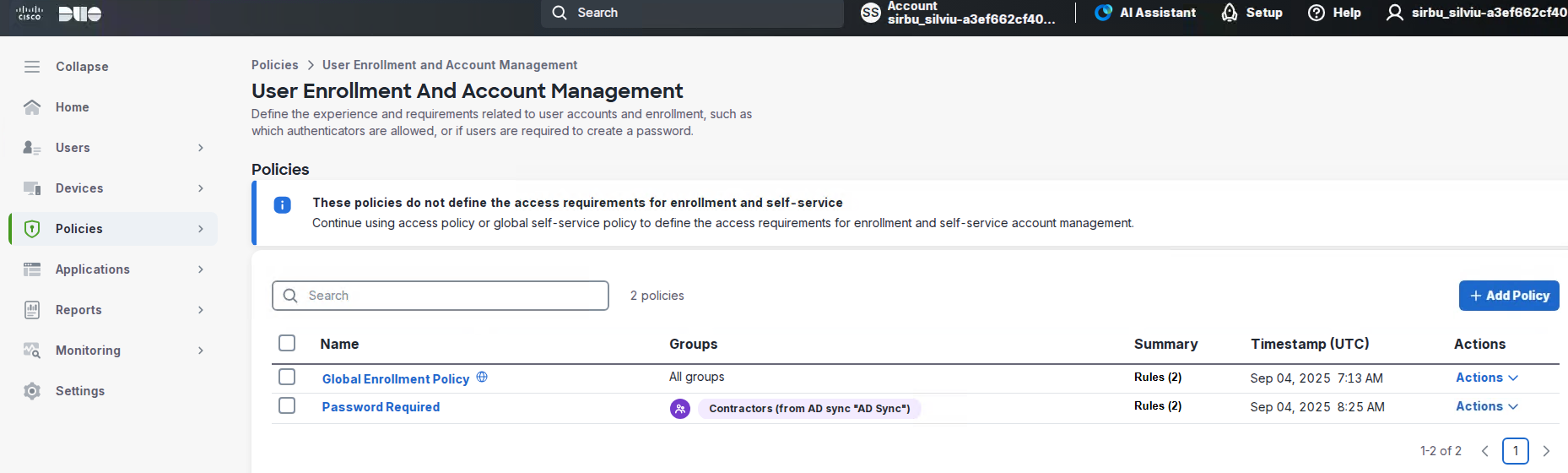
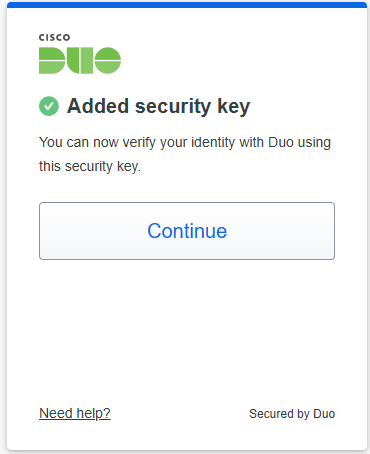
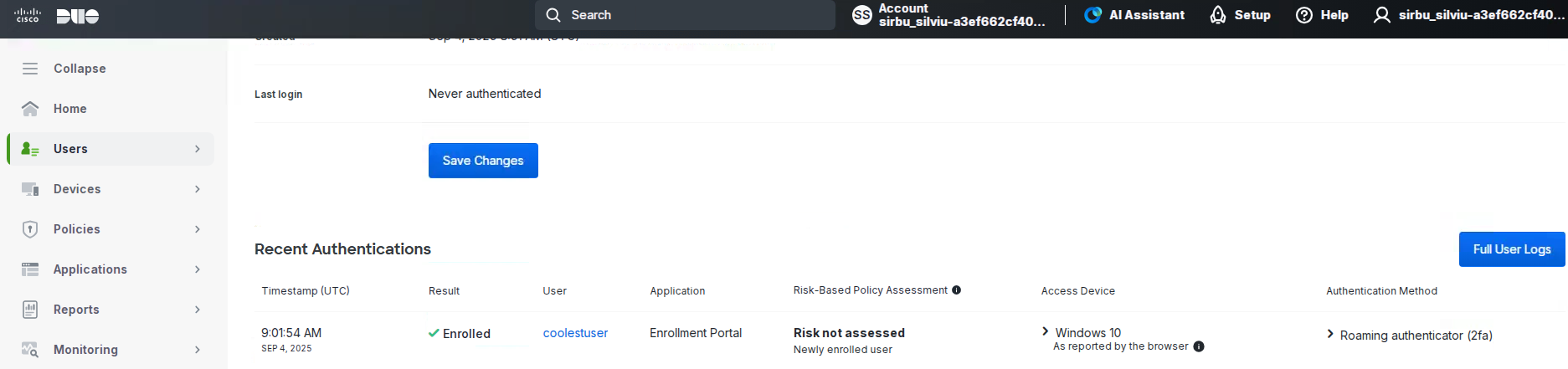
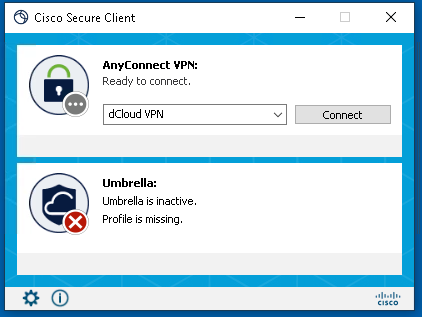
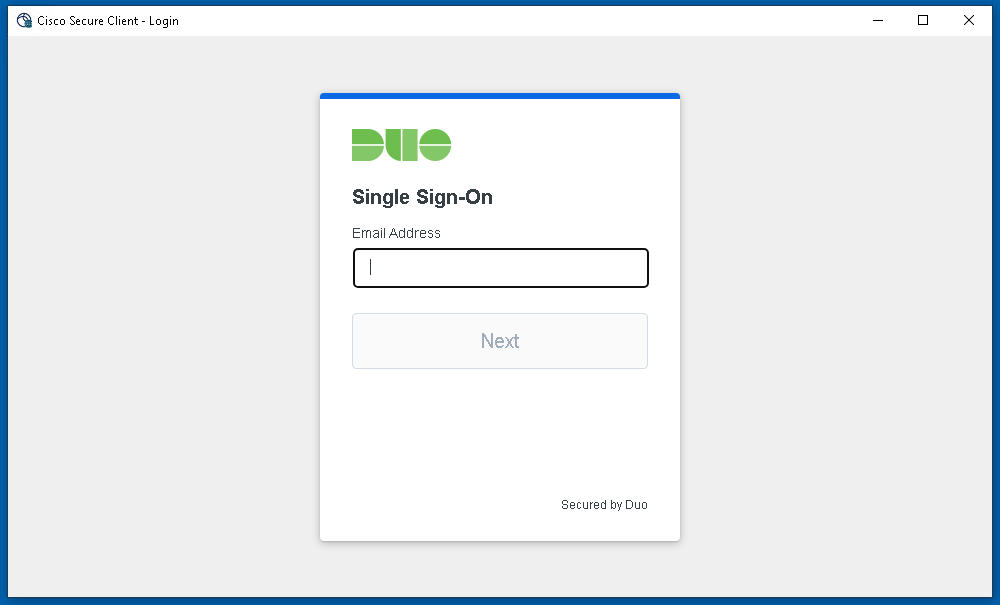
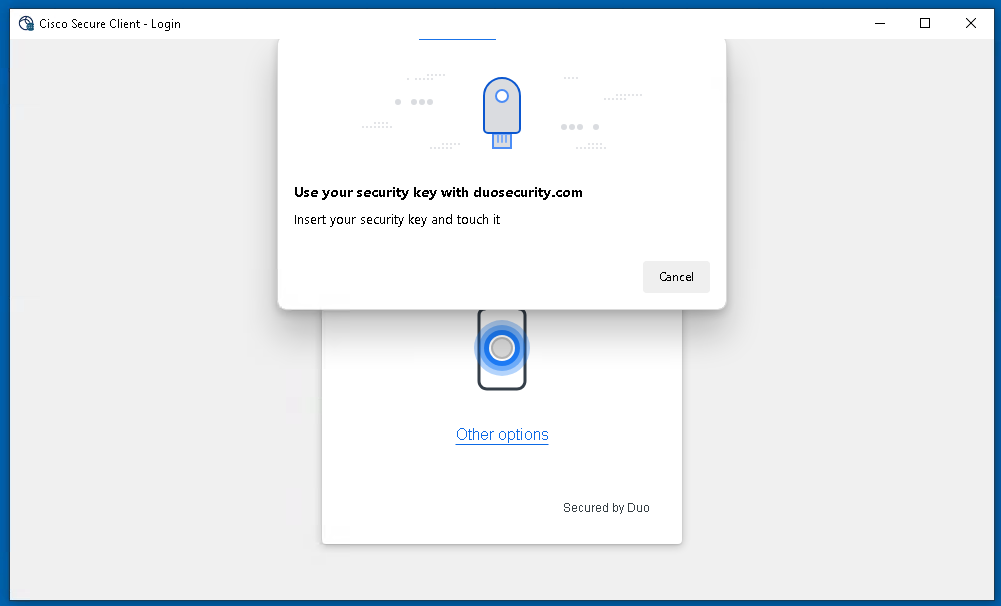
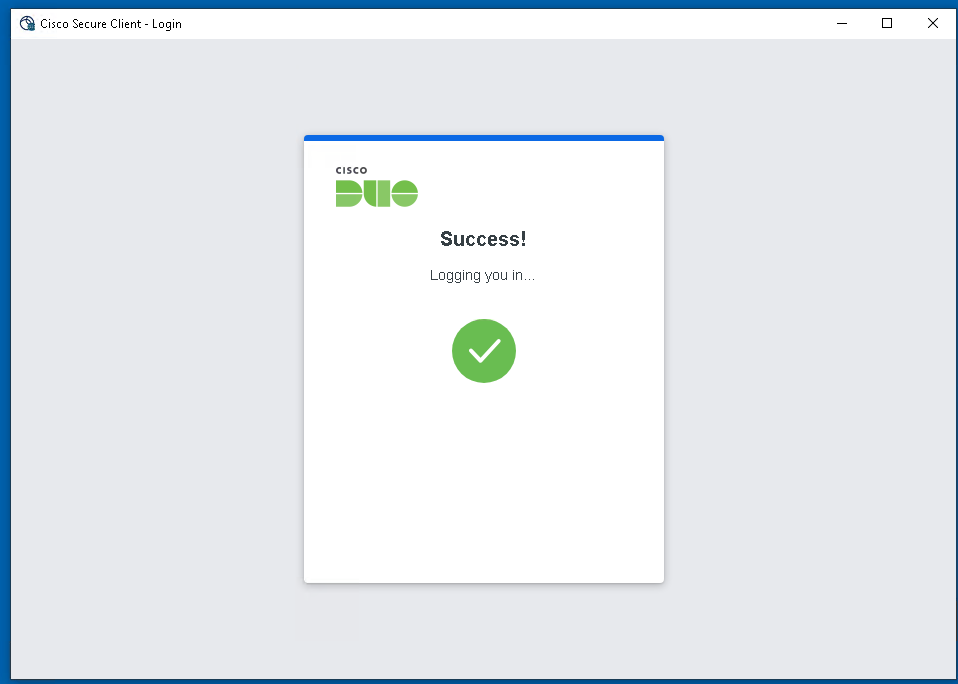
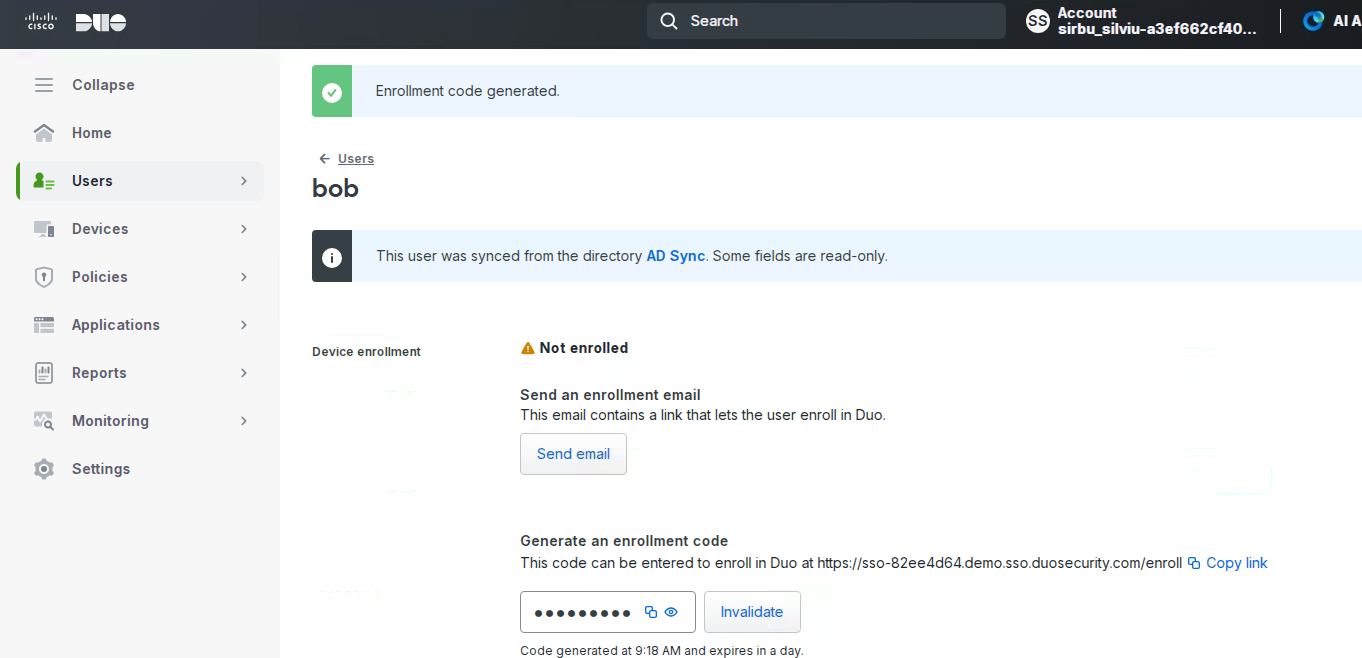
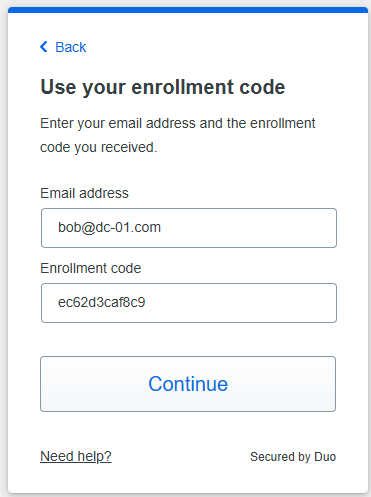
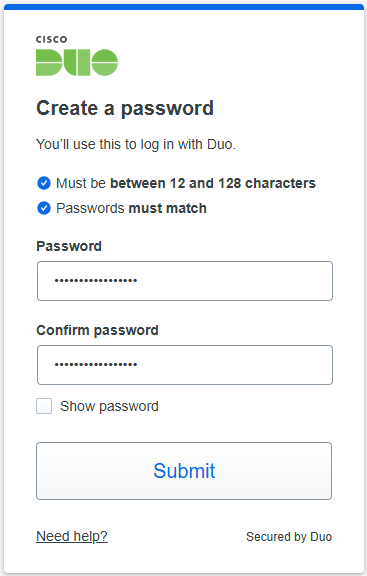
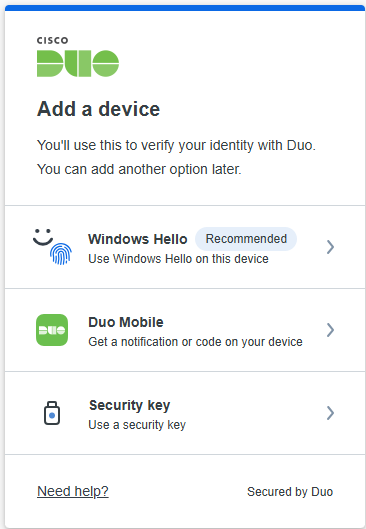
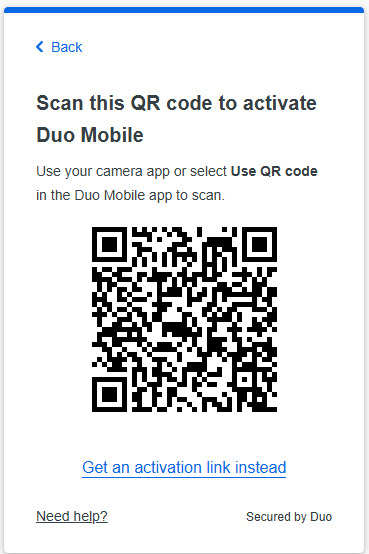
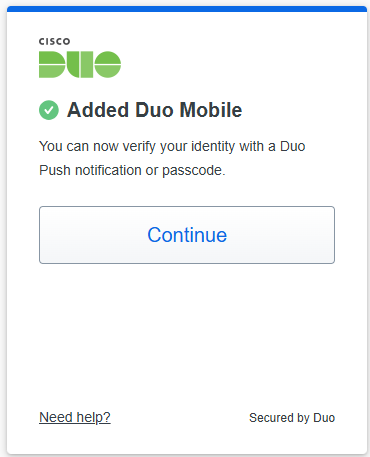
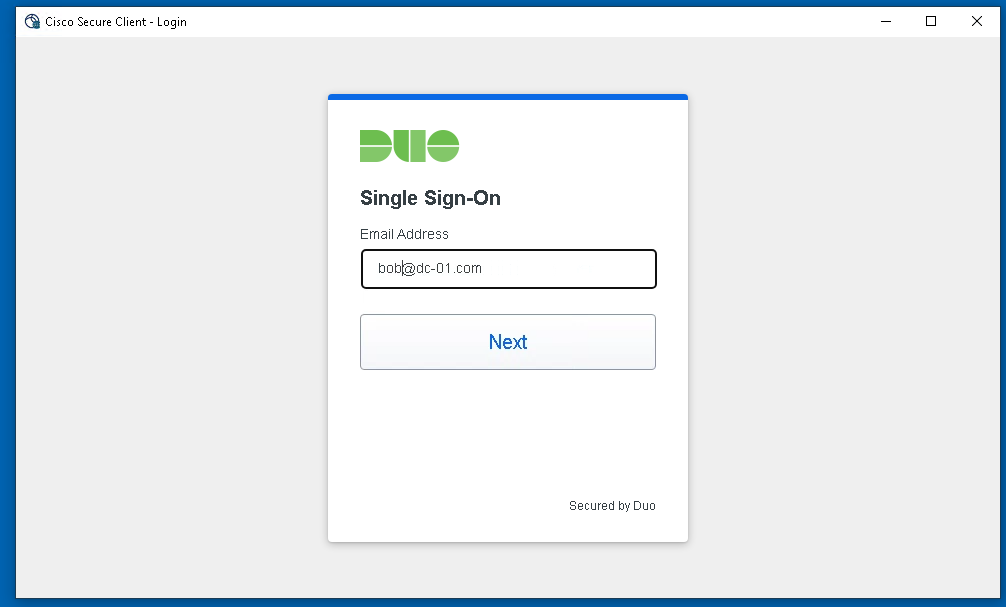
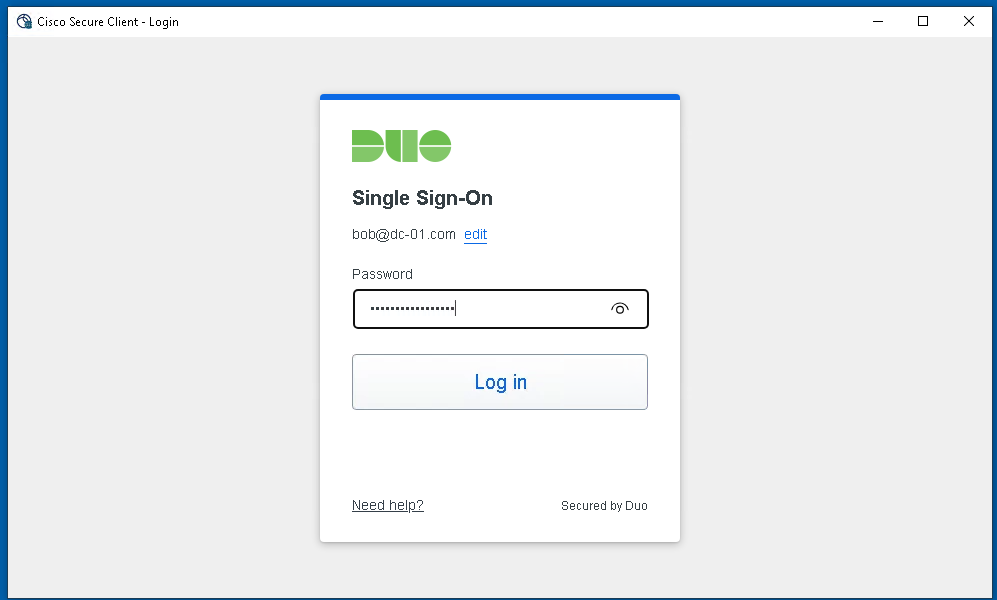
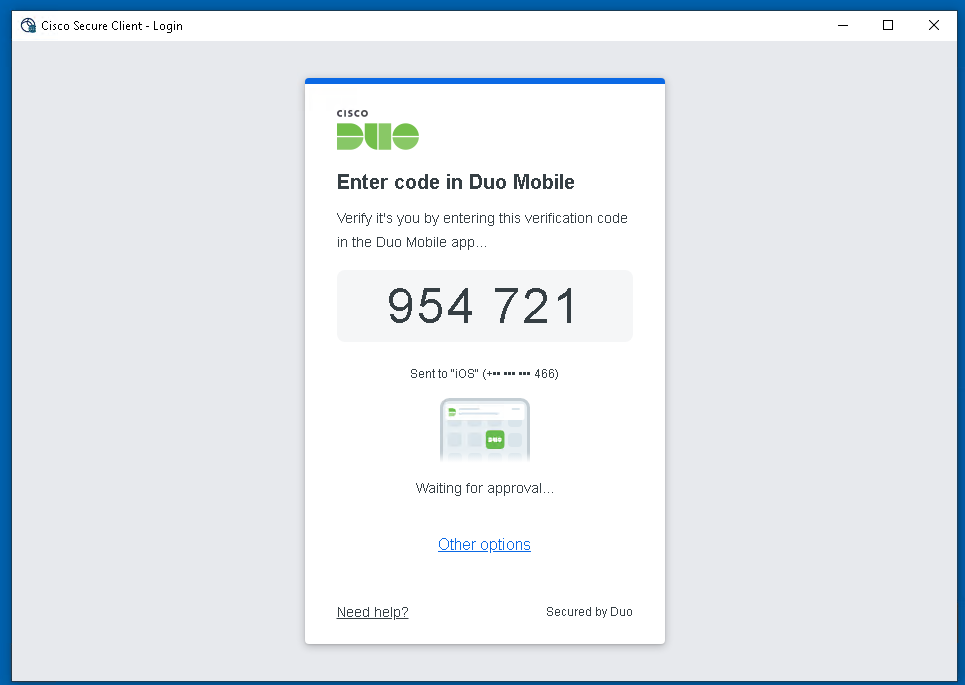
About Cisco DUO Security
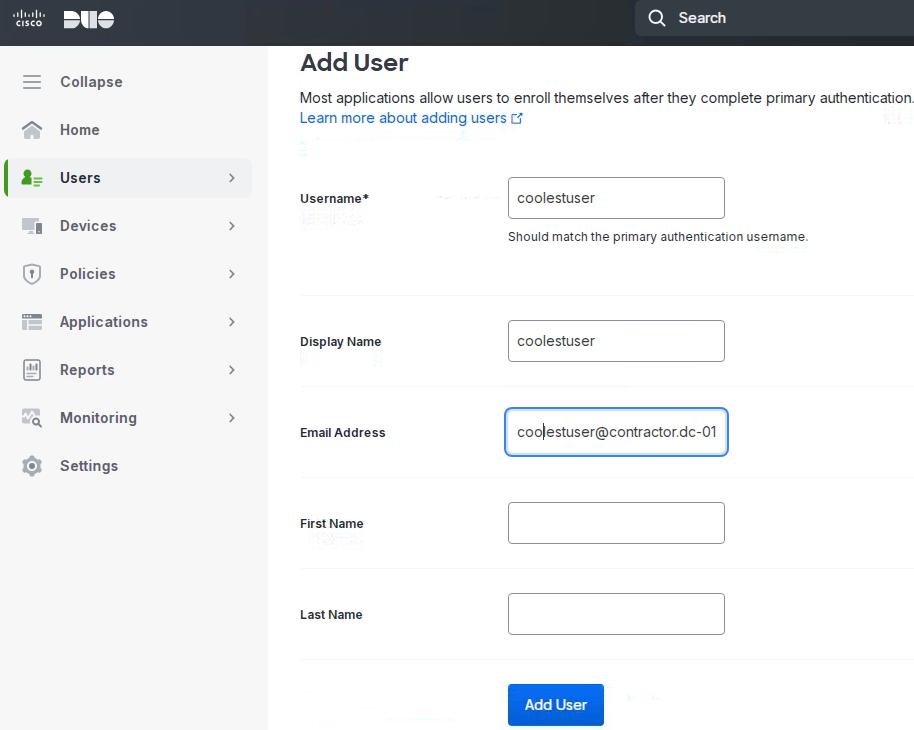
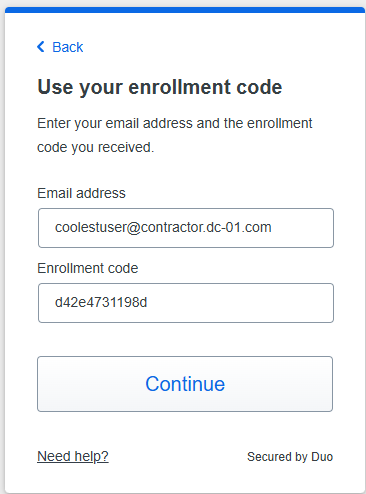
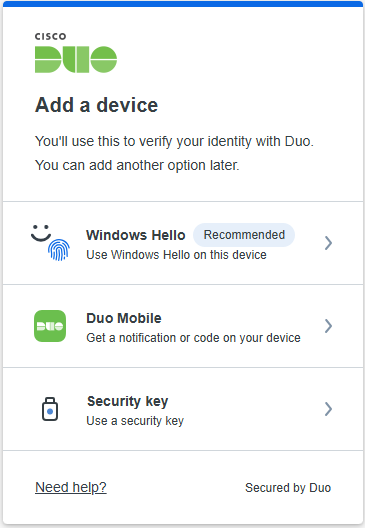
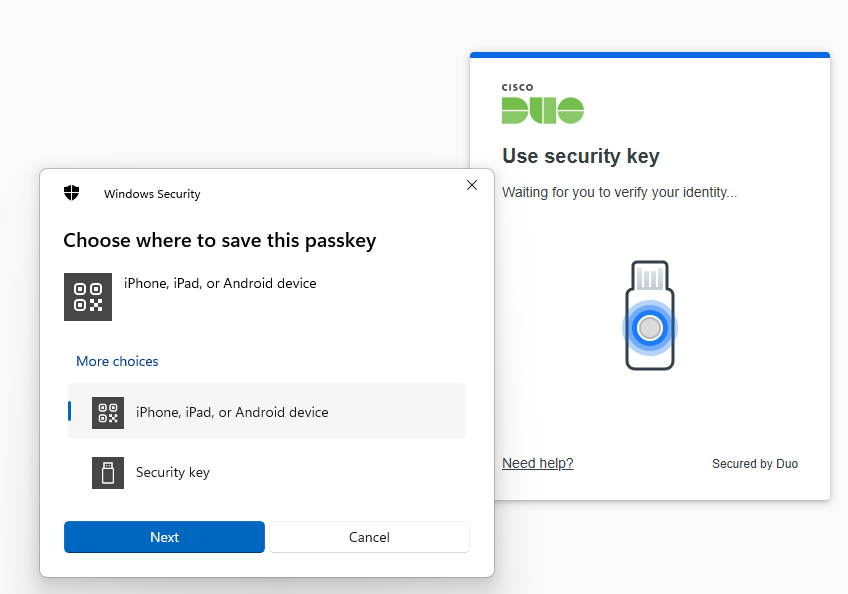
With Cisco Duo, securing your entire organization has never been easier. Cisco Duo’s user directory, flexible authentication options, including passwordless authentication, single sign-on (SSO), granular policy engine, identity automation capabilities, and AI identity analytics deploy fast in any environment. Duo helps keep companies safer than ever before with minimal downtime and optimized productivity.